e-Signatures: What they are and how they work
Electronic signatures go hand in hand with digital transformation. Implementing e-signatures in your business processes eliminates the time-consuming and complex manual signing process of printing out, signing by hand, and scanning every document.
The convenience of the digital signing process also makes it more efficient, while the authentication methods enhance the security and trustworthiness of the process. As the research shows:
“The most common results of implementing e-signature are increased security, productivity and speed. However, most respondents report experiencing more than one significant benefit, including improvements in user experience, revenue gain, availability of legal proof and environmental impact.”
However, some people still hesitate because they’re unaware of the benefits e-signatures provide, or are uncertain about their security or legal validity.
The eIDAS Regulation (the EU’s framework for electronic signatures) categorizes e-signatures into three types. One is a simple electronic signature and the remaining two are classified as digital signatures. E-signature types differ in security levels, regulatory compliance, and technical implementation, making each type applicable in different situations.
So let’s explain the difference between the three e-signature types, and delve deeper into how the digital signing process works. We’ll also explore the benefits of digital signature services for secure document transactions.
Electronic vs. digital signatures – what is the difference?
What is an electronic signature?
While the concepts of electronic and digital signatures are often used interchangeably, they carry many differences that make them applicable to different areas.
An electronic signature, also known as eSignature or e-signature, is a broad category encompassing a range of methods for digitally signing documents.

In the European Union, the eIDAS Regulation defines three types of electronic signatures. It’s important to understand the difference between them as they vary, mostly in terms of security, infrastructure, technical implementation, and regulatory compliance.
The e-signature types are:
- Simple Electronic Signature (SES)
- Advanced Electronic Signature (AES)
- Qualified Electronic Signature (QES)
Simple Electronic Signature (SES) is a basic e-signature type, suitable for routine and less sensitive documents where a high level of security and compliance is not essential. When using SES, there is no need for ID verification; instead, it is enough to know the signer’s email address or have a unique access code before signing. Given its minimal authentication requirements, SES is convenient mostly for signing internal documents or agreements with existing partners.
For transactions involving higher sensitivity levels, the other two e-signature types would be more secure and advanced options: Advanced Electronic Signature and Qualified Electronic Signature, also known as digital signatures.
So why the need to differentiate between digital and simple electronic signatures?
What is a digital signature?
A digital signature is a type of e-signature that acts as an encrypted message to create a barrier against unauthorized tampering, adding an extra layer of security to the signing process. Here’s how Adobe explains the difference:
“A digital signature is a specific type of signature that is backed by a digital certificate, providing proof of your identity. Digital signatures are recognized as being a more secure type of e-signature because they’re cryptographically bound to the signed document and can be verified.”
As regulated by eIDAS, Advanced Electronic Signature and Qualified Electronic Signature comply with digital signature standards. Unlike SES, AES and QES involve authentication measures to confirm the identity of the signer and the integrity of the signed document’s content. They provide a higher level of security, for cases when strong authentication and non-repudiation are necessary.
Advanced electronic signature provides additional security features by adding identity verification. AES relies on digital certificates that identify the signer, ensuring:
- Higher integrity: Any attempt to tamper with the signature, or changes made to the document after applying the signature, are detectable.
- Authenticity: AES verifies the signer’s identity through an authentication mechanism, such as multi-factor authentication, biometric verification, or digital certificates.
- Non-repudiation: It ensures that the signer cannot later deny their involvement or approval of the signed document.
AES is uniquely linked to the signer, so its use adds trust to digital transactions, making them suitable for a wide range of document types, such as legal contracts or sensitive business agreements.
Qualified electronic signature is the most stringent e-signature type and the only one with legal recognition across all EU member states. According to eIDAS, a QES is considered legally equivalent to a handwritten signature and is admissible as evidence in legal proceedings.
In addition to AES’s methods, QES verifies the signer’s identity through face-to-face or video verification. It ensures document integrity and guarantees non-repudiation through the use of qualified digital certificates, issued by Qualified Trust Service Providers (QTSP).
QESs are reserved for strictly regulated agreements requiring the highest security level, legal acceptance, or cross-border recognition. As the regulations may vary in different regions, it’s important to be aware of local laws regarding e-signatures and trust services in order to comply with them.
Now, let’s learn more about how this level of security is achieved.
Digital signatures – how do they work?
When talking about the technological aspects of digital signatures, several interconnected terms come into play, such as Public Key Infrastructure (PKI), digital certificates, and asymmetric cryptography.
Let’s break down these terms to understand their relevance to digital signatures.
Digital signatures are based on Public Key Infrastructure (PKI). PKI is a framework that manages digital keys and certificates to provide secure communication and authentication in a networked environment.
To verify the signer’s identity and ensure the integrity of the signed document, PKI relies on digital certificates, issued by trusted entities known as Certificate Authorities (CAs). A digital certificate contains various pieces of information, including the public key of the certificate holder.
Digital certificates are based on asymmetric cryptography, which involves a pair of keys:
- Public Key: This key is openly shared. It is associated with the signer’s identity and included in a digital certificate.
- Private Key: Known only to the signer, a private key is used for creating digital signatures and must be kept confidential.
Through the process of encryption and decryption, PKI ensures secure data transfer in electronic transactions. In simple words – what one key encrypts, only the other key from the pair can decrypt.
A digital signing process begins with a mathematical summary of the content, called a hash code (a fixed-size string of characters generated from input data of any size). In the context of digital signatures, a hash code is computed from the message or data that needs to be signed.
Here’s how the signing process works within this framework:
1. A private key is used for signing the document:
When a user wants to sign a digital document, they create a digital signature by encrypting the hash code with their private key. The private key ensures that only its holder could have created the signature. It is also an assurance for non-repudiation, meaning that the sender cannot later deny having signed the message, as the private key is known only to them.
2. A corresponding public key is used for verifying the signature:
To verify the signature, the recipient uses the sender’s public key, obtained either from the certificate itself or a trusted source. The recipient decrypts the signature with the public key to obtain the original hash code. Then, the recipient computes the hash code of the received message and compares it with the decrypted hash code. If the codes match, the message has not been altered and was indeed signed by the private key holder.
The combination of these techniques provides a secure way to verify the integrity and authenticity of digital signatures in a non-repudiable manner.
Why use a digital signature service?
To create a proper digital signature, you can use digital signature software. Such services rely on multiple technologies to help businesses streamline the signing process. Digital signature tools enable you to sign documents online from any device or location, resulting in:
- elimination of paperwork
- acceleration of the signing process
- prevention of delays in the process
- time and cost savings.
In fact, research shows that with mobile-friendly signing tools, 44% of signatures are completed in less than 15 minutes.
However, even though the digital signing process offers many benefits, the digital work environment isn’t without its risks. To prevent document tampering or the potential leakage of confidential data, businesses must verify and authenticate signatures, ensuring that their communications are trusted and data delivered securely. Through the technology that relies on digital certificates, digital signature services verify the signer’s identity and ensure the integrity of the signed document.
So the results of using digital signature solutions are:
- faster and more convenient signing process
- trusted and secure business document transactions.
Consequently, using such services, companies can increase their productivity and improve overall document management, especially when integrating them with other tools to automate workflows, increase efficiency, and save time.
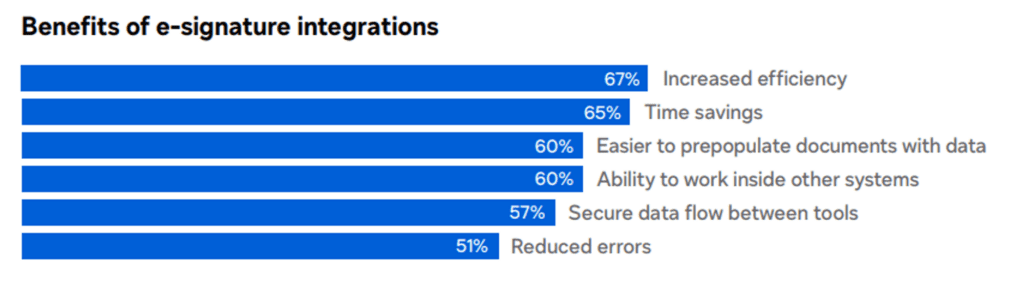
It’s important to note that if you create digital signatures without using a dedicated service, you are responsible for managing your key pairs securely, ensuring the confidentiality of your private key, and maintaining the integrity of the entire signing process. Digital signature services often handle these aspects automatically, offering a more user-friendly and secure experience.
Conclusion
Undoubtedly, electronic signatures significantly benefit businesses by enhancing the efficiency, convenience, and cost-effectiveness of the signing process. However, it is crucial to prioritize the confidentiality of business documents through a trusted and secure digital signing process.
Digital signature services not only streamline the signing process by eliminating paperwork and preventing unnecessary delays but also employ a combination of techniques to verify the authenticity of digital signatures and the integrity of the content.
The eIDAS Regulation categorizes e-signatures into three types: SES for routine documents without stringent security requirements, and AES and QES with robust security measures for sensitive business transactions. Among the three types, QES offers the highest level of security, carrying the same legal effect as a handwritten signature. Understanding these distinctions is essential for applying e-signatures effectively — with the appropriate security level and legal compliance.
To optimize and streamline your business operations, leverage the advantages of electronic signatures along with information management solutions. Combining e-signatures with platforms like M-Files accelerates processes, enhances productivity and security, and minimizes errors. Discover here how these solutions can elevate your business processes.
REFERENCES:
DocuSign | No.1 in Electronic Signature and Contract Lifecycle Management
Free, Legally Binding Electronic Signatures | Signaturely
SSL Certificates & Certificate Lifecycle Management Solutions | Sectigo® Official



